A New Path for Cross-Chain Information: LayerZero and EigenLayer Launch CryptoEconomic DVN Framework
TechFlow Selected TechFlow Selected

A New Path for Cross-Chain Information: LayerZero and EigenLayer Launch CryptoEconomic DVN Framework
The main innovation of the CryptoEconomic DVN Framework lies in providing core components for DVNs through AVS, defining staked assets and penalty mechanisms.
Author: YBB Capital Researcher Ac-Core

TL;DR
● The CryptoEconomic DVN Framework integrates LayerZero's cross-chain message passing with EigenLayer’s economic security and incentives;
● The DVN framework operates through a structured process divided into three main phases: validation, dispute, and slashing;
● By partnering with EigenLayer, LayerZero further decentralizes its DVN, accepting ETH, ZRO, and EIGEN as staking assets, creating new growth flywheels for both ecosystems;
● The CryptoEconomic DVN Framework could enhance overall cross-chain security in the future.
1. Understanding the Narrative: EigenLayer and LayerZero’s Evolution

Image Source: LayerZero Official
On October 2, 2024, LayerZero Labs and Eigen Labs announced the launch of the CryptoEconomic Decentralized Verification Network (DVN) Framework, designed to provide cryptoeconomic security for omnichain messaging. Under this framework, developers can deploy their own DVNs on EigenLayer and leverage incentive mechanisms to strengthen the security and reliability of cross-chain message transmission.
In short, the CryptoEconomic DVN Framework combines LayerZero’s cross-chain security mechanisms with EigenLayer’s restaking-based cryptoeconomic model. Its core objective is to use EigenLayer’s cryptoeconomic model to deliver enhanced security and incentives for decentralized verification networks (DVNs).
1.1 LayerZero V2: Laying the Groundwork for Cross-Chain Mechanisms
LayerZero is not merely an asset bridge but a trustless cross-chain communication protocol that separates the ultimate trust assumption by decoupling relayers and oracles, achieving cross-chain messaging via a super-light client mechanism.
The core architecture of LayerZero V2 consists of three components: Protocol, Standards, and Infrastructure.
1. Protocol
The protocol layer of LayerZero remains consistent across all supported blockchains and features immutability and permissionless access, ensuring censorship resistance and long-term stability. It comprises two primary components:
● Endpoints: Immutable and non-upgradable smart contracts deployed on each blockchain, serving as the core of the LayerZero protocol. Endpoints offer standardized interfaces for applications to manage security configurations and send/receive cross-chain messages. Due to their immutability, once deployed, no entity can alter them;
● MessageLibs: Connected to endpoints, MessageLibs handle the verification and communication of cross-chain messages. Updates to MessageLibs are additive—old versions are never replaced—ensuring backward compatibility. Developers can continue using older versions even as new ones are released, similar to maintaining multiple versions of smart contracts on a blockchain.
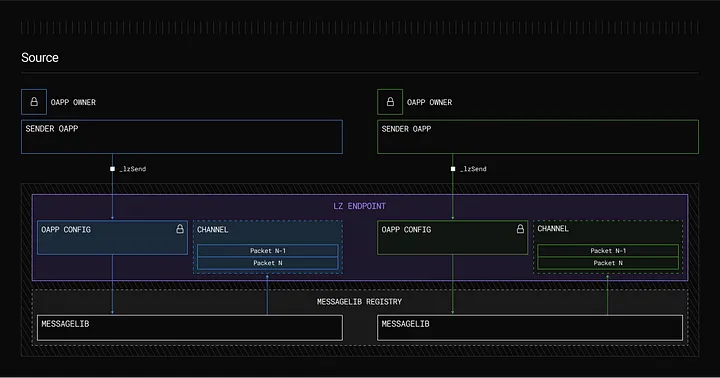
Image Source: LayerZero Endpoint Description
2. Standards
LayerZero’s standards enable developers to build applications and tokens that behave consistently across multiple blockchains, achieving “unified semantics” where apps or tokens exhibit identical behavior regardless of the underlying chain. These standards simplify development and ensure consistency and scalability for omnichain applications.
● Contract Standards: LayerZero provides standards such as OApp (Omnichain Application) and OFT (Omnichain Fungible Token). These extend existing smart contract standards (e.g., OFT extends ERC-20), enabling rapid development of applications and tokens deployable across all LayerZero-supported chains;
● Message Packets: Used to transmit data and commands between blockchains. Packets include elements to prevent replay attacks and misrouting (e.g., Nonce, source/destination chain IDs, unique identifiers) and carry the payload—the actual command or data to be executed on the target chain. This format is adaptable to various environments (EVM/non-EVM, public/private chains), ensuring accurate and secure cross-chain communication;
● Design Patterns: LayerZero offers design patterns (e.g., AB, ABA, Composite AB) that serve as foundational building blocks for developers, simplifying the creation of complex cross-chain interactions. These patterns help build seamless user experiences, such as completing a cross-chain token swap within a single transaction.
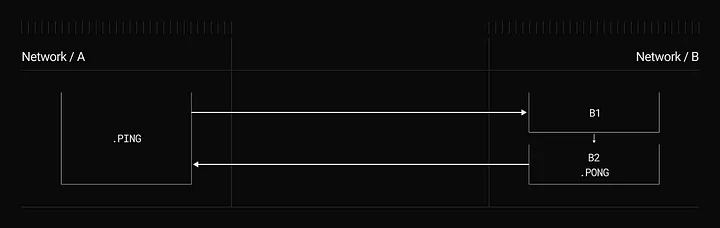
Image Source: Composite ABA Design Pattern
3. Infrastructure
LayerZero’s infrastructure layer is fully permissionless and modular—any entity can join the network to verify and execute transactions. This design allows applications to select customized verification and execution methods, optimizing trade-offs between security, cost, and speed.
● Decentralized Verification Networks (DVNs): These networks validate cross-chain messages. Any entity capable of verifying cross-chain packets can become a DVN. This decentralization enables applications to choose optimal validator combinations, avoiding vendor lock-in. Over 15 DVNs currently participate in LayerZero, including zkLight clients provided by Google Cloud and Polyhedra;
● Executors: Any entity can operate as an executor, responsible for ensuring smooth execution of cross-chain messages on the destination chain. Executors improve UX by allowing users to pay gas fees only on the source chain, eliminating the need for additional actions on the target chain. Applications can select one or more executors, self-host their own, or manually execute messages;
● Security Stack: Each application can configure a custom security stack—including selected DVNs, executors, and other preferences. This flexibility allows applications to tailor their verification processes and adjust them as needed, avoiding reliance on a one-size-fits-all security model.
To better understand the CryptoEconomic DVN Framework, here is additional context on LayerZero V2’s DVN:
Decentralized Verification Networks (DVNs) verify messages transmitted across different blockchain networks. Every application built on LayerZero can customize its security stack by selecting DVNs. Key points include: 1. DVNs: Entities responsible for validating cross-chain messages, ensuring their security and integrity. Developers can configure which DVNs to use and set optional validation thresholds. 2. Openness: Anyone can create or develop a DVN, offering diverse validation methods. DVNs may include validators, signers, or advanced technologies like zero-knowledge proofs (ZKP) or middleware chains. 3. Customizable Security: Applications can select DVNs based on their specific security needs. Unlike rigid, uniform models, this flexibility allows tailored security configurations, reducing costs and risks. 4. DVN Combinations: Using an “X of Y of N” configuration, applications can require multiple DVNs for message validation. For example, a “1 of 3 of 5” setup means one specific DVN plus any two others from a pool of five must validate the message.
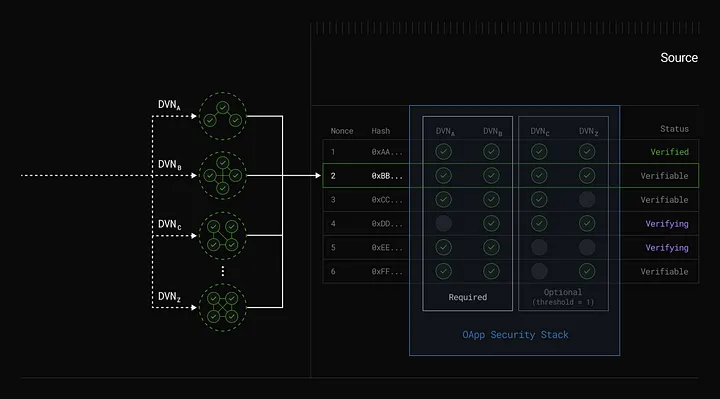
Image Source: DVN Position in V2 Architecture
1.2 EigenLayer: The Cryptoeconomic Backbone of CryptoEconomic DVN
EigenLayer consists of a suite of smart contracts that allow users to “restake” their ETH or liquid staking tokens (LSTs) to bootstrap new proof-of-stake (PoS) networks and services within the Ethereum ecosystem. In return, users earn additional staking rewards while providing security and decentralization to modular components and other blockchain networks. In essence, EigenLayer monetizes Ethereum’s security. More specifically, EigenLayer establishes five key categories: native restaking, LRT, AVS, hyperscale rollups, and composable applications.
1. Native Restaking
Enables simultaneous validation commitments, measures the cryptoeconomic bandwidth consumed by each commitment, and ensures all commitments remain solvent. It represents Ethereum’s “elastic scaling of security” (ES2)—if conditions for each AVS are met, they can all be secured;
2. Liquidity Restaking
LRT is a mechanism where liquidity restaking tokens (LRTs) represent assets deposited into EigenLayer, analogous to liquid staking tokens (LSDs) on Ethereum, thus unlocking otherwise illiquid capital;
3. AVS Economy
The core of EigenLayer, representing a collection of decentralized systems that pair technology with varying degrees of decentralized trust architectures. An AVS-centric roadmap ensures permissionless decentralized services can integrate seamlessly to support arbitrary applications, enabling diverse and customizable AVS deployments on EigenLayer;
4. Hyperscale Rollups
Most crypto application development remains constrained by blockspace limitations. Without a scalable cloud-like infrastructure, innovation is hindered.
For example, EigenDA provides a mechanism for infinite bandwidth scalability, enabling previously impossible use cases—essentially transforming cloud infrastructure into cryptographic primitives;
5. Composable Trustable Applications
EigenLayer aims to maximize the number of enforceable commitments. EigenLayer + Ethereum delivers Ethereum-grade diversity and verifiable commitments. For instance: 1. Maximizing effect via EigenDA; 2. Achieving diversity through open innovation in EigenLayer AVS; 3. Introducing off-chain verifiability on-chain for verifiable computation.
2. Tokenomics Synergy: LayerZero x EigenLayer – ZRO and EIGEN as Staking Assets
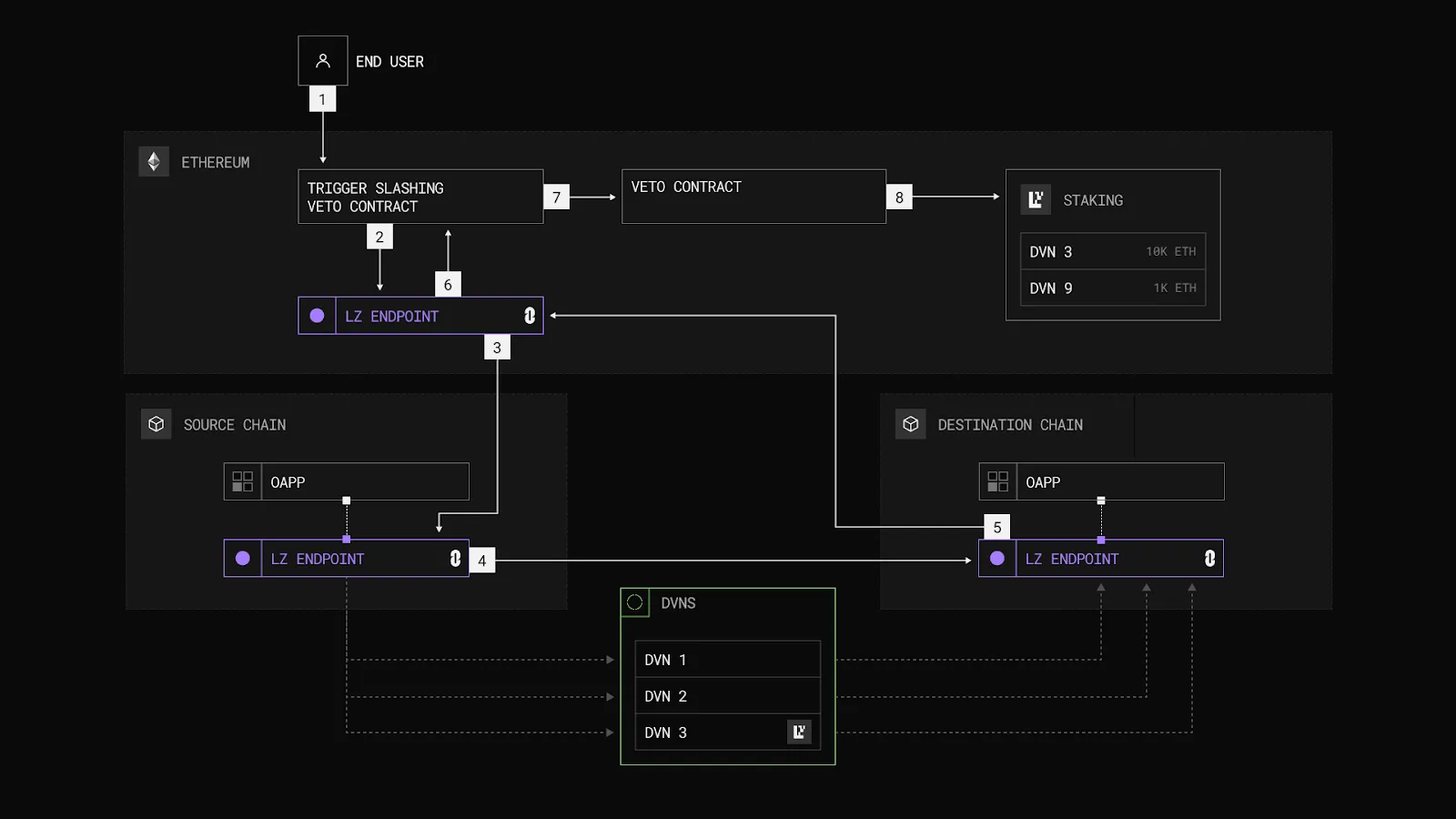
Image Source: Illustrating Staking, Validation, Dispute, and Slashing Process
In short, the CryptoEconomic Distributed Verification Network (DVNs) enhances cross-chain security through three key mechanisms:
1. Cryptoeconomic Security: DVNs introduce slashing penalties—if a DVN acts maliciously or incorrectly, its staked assets are penalized. This economic model ensures DVNs have strong financial incentives to behave honestly, as misconduct leads to significant financial loss, thereby reinforcing accountability and security;
2. AVS-Defined Security: Each Active Verification Service (AVS) defines acceptable staking assets and associated slashing conditions. This flexibility allows different types of DVNs (e.g., ZKP-based, Middlechain, or PoA) to strengthen their security with additional staking collateral, increasing economic deterrence against malice;
3. Permissionless Security: Anyone can contribute to a DVN’s security by staking assets, making the system more open and participatory. DVNs can accept various assets (e.g., ZRO, ETH, EIGEN) as collateral, broadening security options and enhancing decentralization.
The CryptoEconomic DVN Framework is an open-source system designed to enhance the security of decentralized verification networks (DVNs) through token-backed economic incentives. It builds upon LayerZero’s DVN message verification and adds an extra security layer. It protects LayerZero’s cross-chain messaging through four key mechanisms: Staking, Validation, Dispute, and Slashing.
1. Staking: Validators (stakers) lock tokens such as ZRO, EIGEN, or ETH into the DVN’s Active Verification Set (AVS) as collateral. This stake incentivizes honest behavior, as misconduct may result in slashing;
2. Validation: Users or applications can trigger a round-trip cross-chain message (Ethereum → source chain → destination chain → Ethereum) to verify whether the hash recorded by the DVN matches the on-chain hash. If they match, the process ends;
3. Dispute: If a mismatch is detected, a dispute process begins, allowing token holders to vote on whether to slash the DVN’s stake. This prevents false slashing due to non-malicious errors such as blockchain reorgs, which might cause packet mismatches even if the DVN acted honestly;
4. Slashing: If the dispute fails and malicious behavior or incorrect validation is confirmed, the DVN’s staked assets are slashed.
The framework operates in three stages:
● Stage 1: Validation – Messages are verified across multiple chains using independent DVNs to ensure impartiality;
● Stage 2: Dispute – If discrepancies are found, a dispute contract is triggered, and token holders vote on whether to slash the DVN’s stake;
● Stage 3: Slashing – If the dispute fails, the DVN’s stake is slashed for malicious behavior or faulty validation.
3. Perspective on the CryptoEconomic DVN Framework

Ethereum’s infrastructure has matured, and a multi-chain reality is now established. However, cross-chain communication security remains a critical challenge. The main innovation of the CryptoEconomic DVN Framework lies in leveraging AVS as a core component for DVNs, clearly defining staking assets and slashing mechanisms. In the long term, it may significantly improve overall chain security. Yet, the potential uncertainties mirror industry-wide concerns—finding the right balance between security and flexibility remains a key challenge moving forward.
Undoubtedly, the CryptoEconomic DVN Framework represents a mutually beneficial collaboration between LayerZero Labs and Eigen Labs. From a technical standpoint, it ensures security through staking, slashing, validation, and dispute mechanisms. But economically, it reflects another layer of PoS yield stacking—a recursive incentive structure.
By partnering with EigenLayer, LayerZero deepens the decentralization of its DVN. Accepting ETH, ZRO, and EIGEN as collateral creates new growth flywheels for both token ecosystems. LayerZero provides the technology, EigenLayer brings capital—this synergy rewards validators and encourages honest participation within the economic system.
References:
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News