Exploring Different Approaches to Achieving On-chain Privacy
TechFlow Selected TechFlow Selected

Exploring Different Approaches to Achieving On-chain Privacy
Currently, there are mainly three approaches to achieving on-chain privacy: privacy coins on specific blockchains, stealth pools that conceal assets for a group of users (such as Tornado Cash), and privacy-preserving execution virtual machines.
Author: Elusiv Privacy
Translation: Denglun Community
Public blockchains are transparent by default at the protocol level, with transactions permanently visible and immutable to anyone via the blockchain ledger. Only pseudonymous public key addresses exist, and identifying user identities from these addresses and on-chain activity is relatively straightforward for blockchain analytics firms like Chainalysis or de-anonymization protocols like Arkham. This is precisely why privacy protection is critical for safeguarding users and ensuring applications built on public ledgers remain secure.
Due to their decentralized nature, achieving user privacy guarantees on blockchains is more complex than in Web2 predecessors, which rely on proprietary data centers to secure user data. However, as we know, this model introduces numerous flaws and fosters widespread phenomena such as surveillance capitalism and data exploitation. So how is privacy achieved on blockchains, where networks and applications operate across distributed nodes?
In this article, we will break down several types of privacy-preserving protocols that use various methods to achieve privacy for blockchain users. We will not delve into the cryptographic primitives enabling privacy within these systems—those are explained in other articles.
Different Approaches to Privacy on Blockchains
There are multiple ways to achieve privacy for users of public blockchains—from privacy coins to mixing pools and private execution virtual machines. Each model involves different trade-offs, and understanding them is crucial when using these privacy-enhancing tools or integrating them into new or existing applications.
Asset-Specific Privacy
Asset-specific privacy is one of the earliest forms of on-chain privacy protection. This includes privacy coins like ZCash or Monero, where privacy guarantees are tied to specific assets—ZEC and XMR. These blockchains are built solely for a single digital currency (ZEC for ZCash and XMR for Monero) and transfer use cases. Although there are nuances—for example, ZCash can exist in both private and transparent forms—the general limitation of this approach is that privacy is bound to a specific asset. That is, privacy applies only to the native token. This fundamentally limits usability, as users cannot access privacy for other asset types. While ZCash and Monero are viable options for users wanting to privately send or receive ZEC or XMR, interacting with other blockchain ecosystems and their respective applications becomes difficult. Ecosystems like Ethereum and Solana host hundreds of different asset types, including non-fungible assets such as SBTs and NFTs. As these ecosystems mature, privacy protection must expand to support diverse assets, allowing users to access privacy guarantees for any assets they choose to transact with.
Mixing Pools
Mixing pools, sometimes referred to as anonymity sets or privacy pools, are solutions designed to break the link between a user's public key and the assets they hold, enabling them to transact privately. At a high level, users deposit assets into a pool managed by a smart contract. Through various cryptographic techniques, each user’s deposit becomes indistinguishable from another’s within the mixing pool. After depositing, users can initiate transactions by proving (typically via zero-knowledge proofs) their control over the deposited assets. This allows them to utilize these assets without linking them to their public keys, effectively preserving privacy. A key limitation of mixing pools is that the strength of privacy guarantees depends on the number of unique deposits in a given pool. In short, more users mean stronger privacy.
Private Execution Virtual Machines
Private execution virtual machines (VMs) represent a new form of blockchain privacy protection. This approach enables off-chain computation with on-chain verification, as there is currently no efficient way to directly verify the correctness of private data on-chain. While fully homomorphic encryption may change this in the future, today’s standard uses an off-chain execution, on-chain verification model powered by zero-knowledge proofs. This allows applications and users to avoid publishing any exposed or sensitive data on-chain. By leveraging zero-knowledge proofs for privacy, it eliminates the need to publish data while preserving the correctness of state transitions. This approach supports "privacy-by-default" Layer 1 blockchains like Aleo, or privacy-focused Layer 2s like those developed by Aztec Labs, where privacy can be implemented. Private VMs expand the scope of possible solutions by enabling arbitrary private applications on-chain, such as private gaming. However, privacy guarantees in this architecture are not limited by anonymity sets but rather by state interactivity, which determines how much data a user must reveal to others during interactions that lead to state changes. Additionally, this method has limitations for existing applications, as it requires entirely new logic.
Each privacy protection method on blockchains has its strengths and weaknesses, depending on the use case and application. Privacy coins like ZEC and XMR work well for basic transfers but are constrained by usability. Mixing pools offer greater flexibility for privacy but depend on the volume of deposits within the pool for effectiveness. Private execution VMs lay the foundation for “default-private” possibilities but still carry risks of information leakage and significant development overhead. While each use case and application must carefully consider the ideal design for enhanced privacy, many ecosystems and applications now require privacy.
A Closer Look at Mixing Pools
Mixing pools offer one of the most flexible and effective forms of account-level privacy enhancement. Let’s dive deeper into some nuances of this approach and how Elusiv extends this design through a robust and comprehensive privacy solution that scales across ecosystems.
Measuring Privacy Guarantees Across Different Mixing Pools
Privacy protocols adopt different approaches when implementing mixing pool designs, each bringing distinct trade-offs. Tornado Cash, one of the most well-known Ethereum-based privacy protocols, uses this method to obfuscate on-chain transactions. Although the Tornado Cash application supports various assets, its pools are segmented by asset type. For instance, Pool A might contain only Ethereum cryptocurrency (ETH) deposits, while Pool B holds deposits of a digital dollar stablecoin (USDC). Another leading Ethereum privacy protocol, Aztec, employed a similar method in its zk.money application before discontinuing it in March 2023.
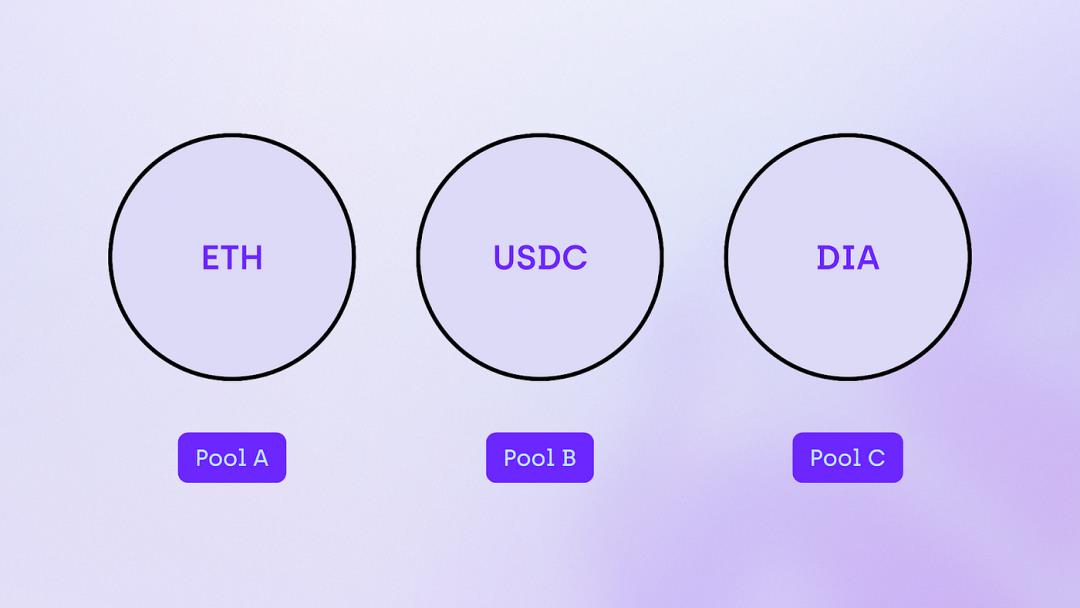
This basic segmentation reduces privacy guarantees because pools are fragmented. The effectiveness of privacy depends on the deposit volume within a specific pool. Consequently, pools associated with higher-market-cap assets (like USDC) provide stronger privacy guarantees compared to those linked to lower-market-cap assets. Fewer deposits make it easier to correlate public keys and their interactions, potentially leading to identification.
Although these applications can protect the privacy of various assets from a user perspective, the inherent fragmentation of mixing pools limits the underlying privacy guarantees. Removing such restrictions would significantly increase the anonymity set, delivering better privacy for all users.
Elusiv’s Multi-Asset Privacy Pool
With its V2 upgrade, Elusiv implements a more flexible privacy pool design, enabling arbitrary assets to share the same privacy set within a Multi-Asset Privacy Pool (MASP). It allows users to privately hold and transfer ownership of assets on general-purpose chains while retaining composability with smart contracts on the underlying base chain. This means users can hold and interact with any asset or application supported by Elusiv’s smart contracts, while benefiting from a larger anonymity set. As a result, privacy guarantees are determined collectively by:
-
Total number of private transactions (private sends and receives)
-
Total number of private DeFi operations (via the Elusiv SDK)
-
Total value locked in the Elusiv smart contract

Elusiv’s MASP provides a universal privacy pool for the entire ecosystem, where users of Elusiv or any application integrated with the Elusiv SDK share the same anonymity set. This is extremely powerful for privacy protection, making it now a comprehensive, non-exclusive privacy tool.
Compliance Considerations
While mixing pools offer sufficient privacy protection for users, the lack of compliance mechanisms to filter illicit activities and distinguish honest users from malicious actors has significantly hindered usability—evidenced by Tornado Cash’s sanctions in 2022. Elusiv comprehensively addresses privacy concerns by implementing Zero-Knowledge Encrypted User Safeguards (ZEUS), a decentralized, privacy-preserving compliance solution designed to prevent any illegal use of Elusiv’s MASP. This not only protects Elusiv and its users but also establishes regulatory alignment, ultimately enabling scalable on-chain privacy protection.
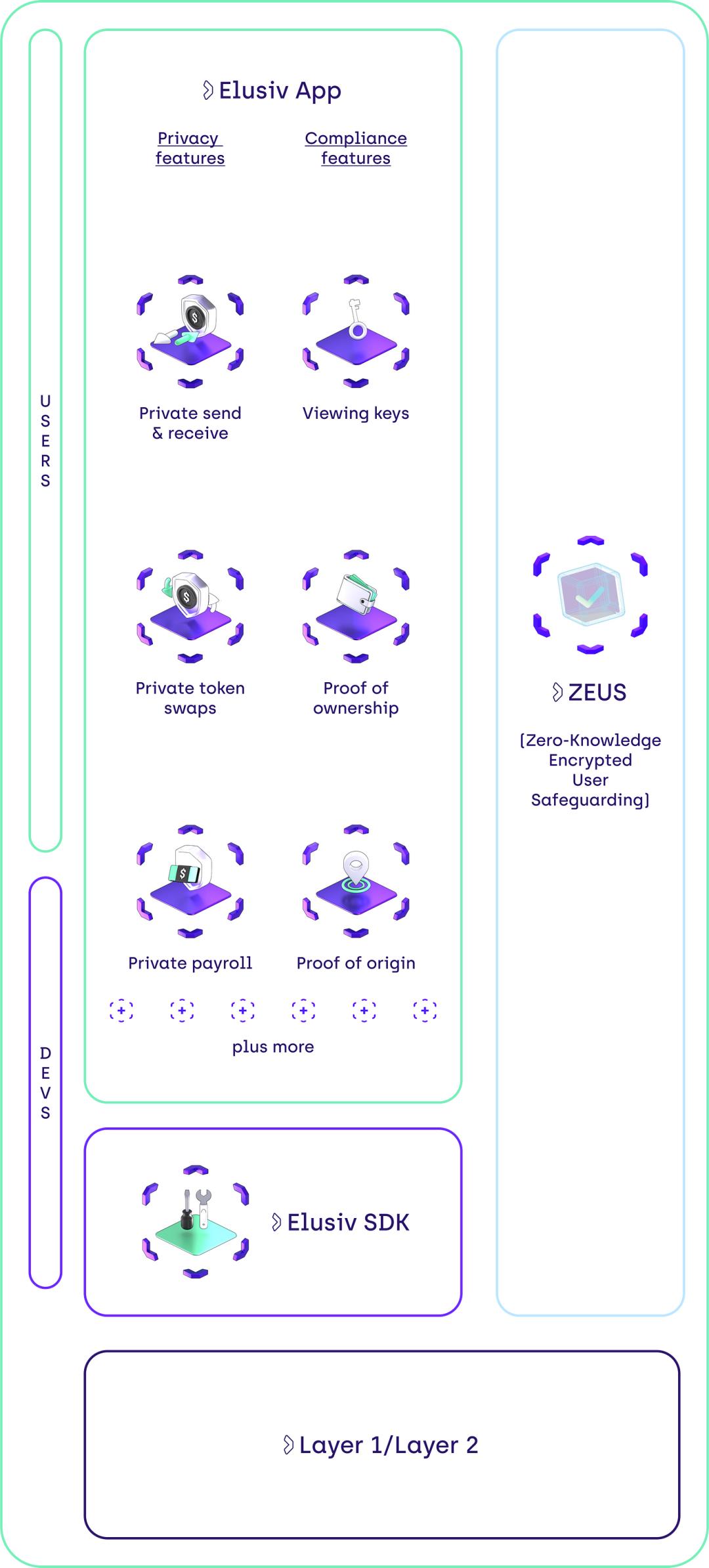
Elusiv Tech Stack
Elusiv Will Redefine Blockchain Privacy
Usable outcomes and widespread adoption of privacy in blockchains have yet to be realized. Why? Beyond compliance, the current privacy landscape is fragmented. Depending on the privacy protocol used, underlying limitations affect either privacy guarantees, user experience, or both. Elusiv aims to deliver compliant, composable, and modular privacy for blockchains. Wallets, decentralized exchanges, lending protocols, and more can integrate Elusiv and leverage its universal privacy pool functionality for entire ecosystems like Solana. Imagine privacy guarantees shared across all applications from a single privacy pool! This introduces a powerful new paradigm—one that fosters flexible, community-driven privacy enhancement, uniting users and applications alike.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News